Audit Scanner - Policy Reports
When using the Kubewarden Audit Scanner, the results of the policy scans are stored using the PolicyReport Custom Resource.
The PolicyReport CRDs are under development in the wg-policy Kubernetes group.
Therefore, this documentation will become out of date if a new version of the CRDs is released.
Check the wg-policy group
repository
for more information about the CRDs.
These CRDs offer a structured way to store and manage the audit results.
Each namespace scanned by the audit scanner has a dedicated PolicyReport resource defined in it.
The results of Cluster wide resources are found in a ClusterPolicyReport object.
There will be only one ClusterPolicyReport per cluster.
The audit results generated by the scanner include:
- the policy that was evaluated
- the resource being scanned
- the result of the evaluation (pass, fail, or skip)
- a timestamp indicating when the evaluation took place.
You can also define severity and category annotations for your policies.
Operators can access the reports via ordinary kubectl commands.
They can also use the optional UI provided by the
policy-reporter
open source project for monitoring and observability of the PolicyReport CRDs.
Policy Reporter UI
The Policy Reporter is shipped as a subchart of kubewarden-controller.
Refer to the Audit Scanner Installation
page for more information.
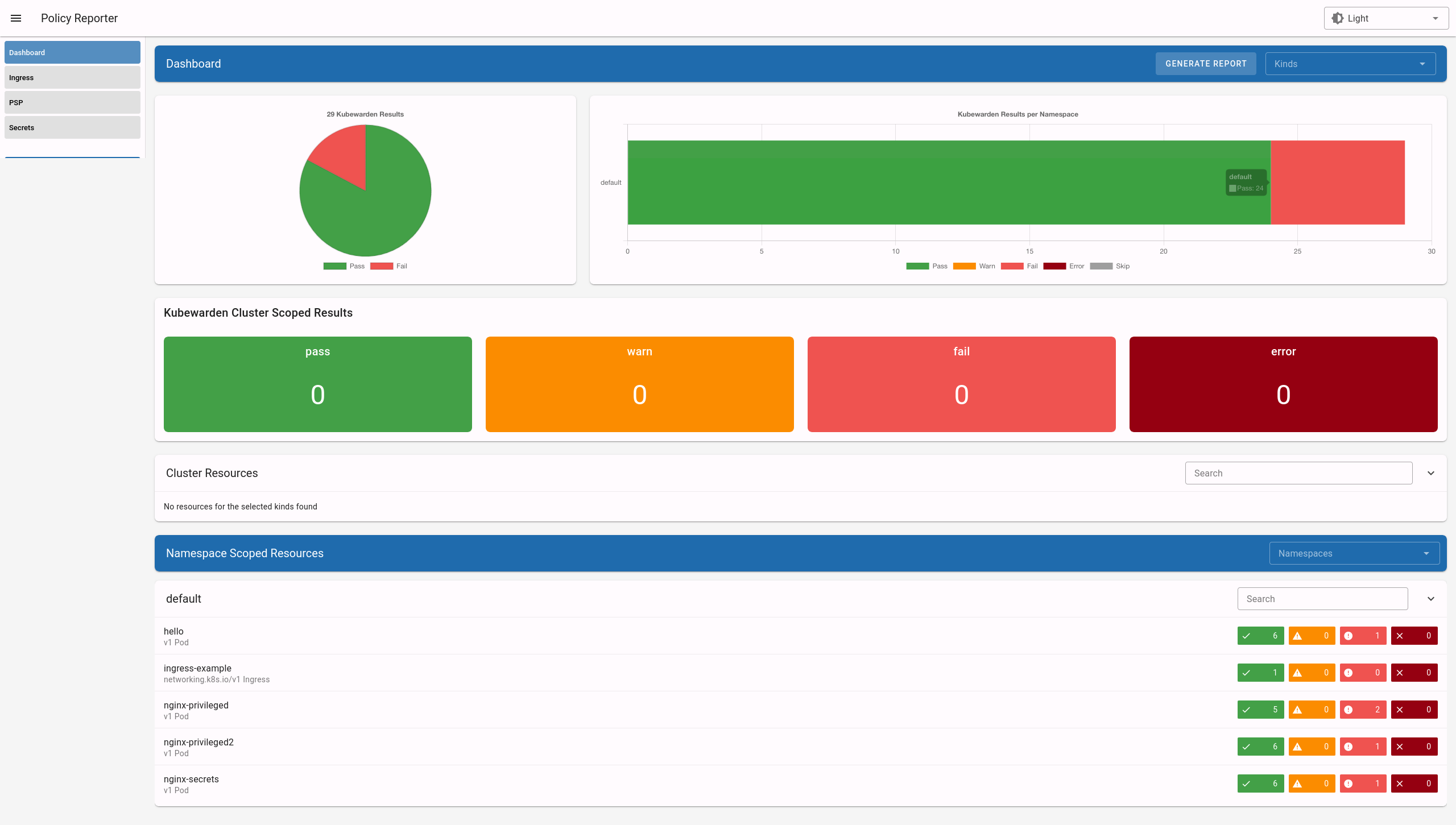
The Policy Reporter UI provides a dashboard showcasing all violations
from PolicyReports and the ClusterPolicyReport.
This is shown below.
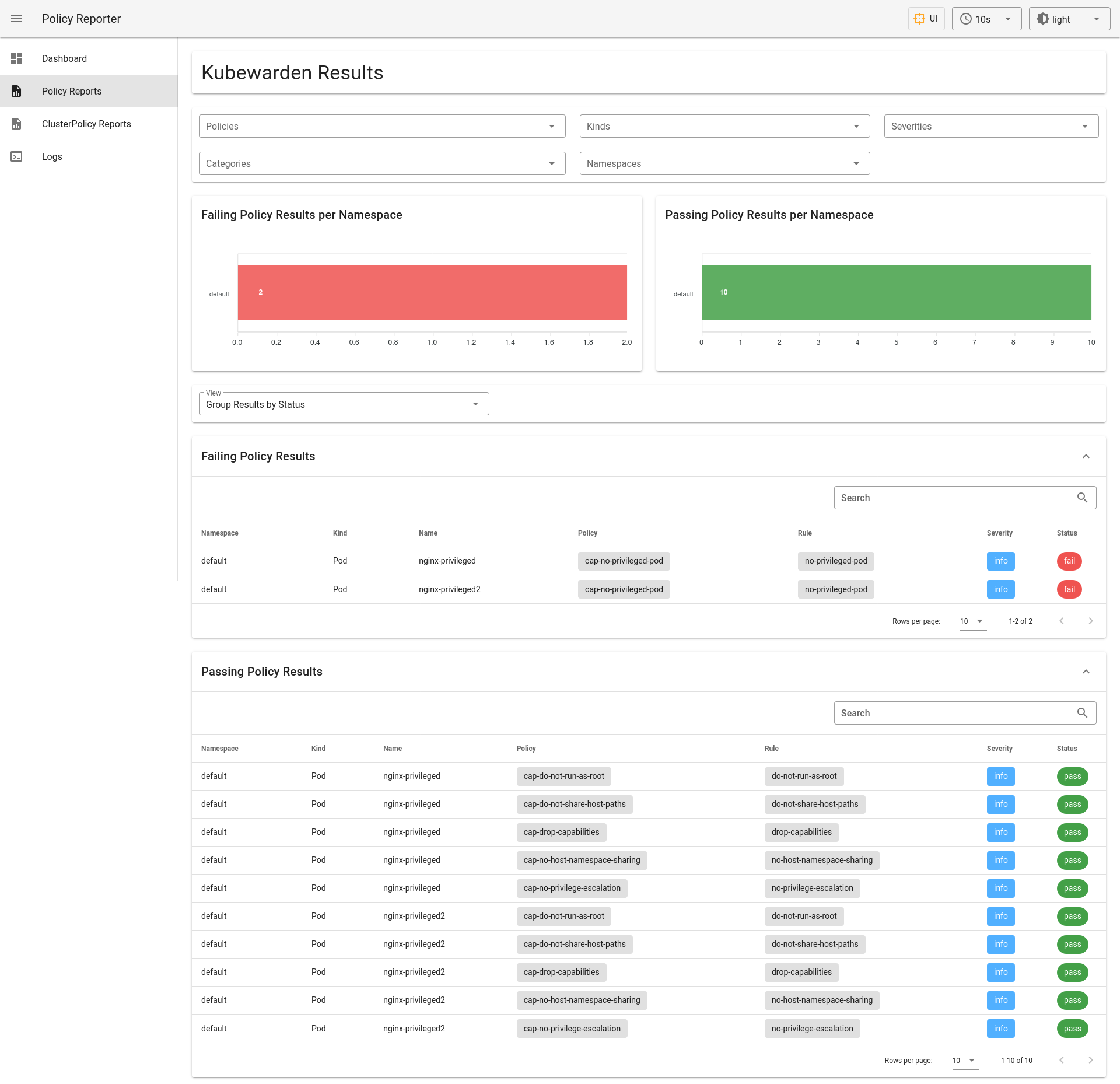
As shown below, it also provides a tab for PolicyReports, and a tab for ClusterPolicyReports, with expanded information.
Other features of Policy Reporter include forwarding of results to different clients (like Grafana Loki, Elasticsearch, chat applications), metrics endpoints, and so on. See the policy-reporter's community docs for more information.
Cluster-Wide Audit Results example
In the next example, the audit scanner has evaluated the cap-testing-cap-policy on many namespaces in the cluster.
The results indicate that all the namespaces passed the policy validation.
The summary section summarizes the audit results, showing there were no errors, failures, or warnings.
apiVersion: wgpolicyk8s.io/v1beta1
kind: ClusterPolicyReport
metadata:
creationTimestamp: "2023-07-10T19:25:40Z"
generation: 1
labels:
app.kubernetes.io/managed-by: kubewarden
...
results:
- policy: cap-testing-cap-policy
...
resourceSelector: {}
resources:
- apiVersion: v1
kind: Namespace
name: kube-system
...
result: pass
rule: testing-cap-policy
source: kubewarden
timestamp:
nanos: 0
seconds: 1689017140
- policy: cap-testing-cap-policy
...
resourceSelector: {}
resources:
- apiVersion: v1
kind: Namespace
name: default
...
result: pass
rule: testing-cap-policy
source: kubewarden
timestamp:
nanos: 0
seconds: 1689017140
...
summary:
error: 0
fail: 0
pass: 6
skip: 0
warn: 0
Namespace-Specific Audit Results example
In this example, the audit scanner evaluated many policies on resources within the default namespace.
The results indicate that certain resources failed the validation for the cap-no-privilege-escalation policy.
Others passed the validation for the cap-do-not-run-as-root policy.
The summary section shows the number of failures and passes.
apiVersion: wgpolicyk8s.io/v1beta1
kind: PolicyReport
metadata:
creationTimestamp: "2023-07-10T19:28:05Z"
generation: 4
labels:
app.kubernetes.io/managed-by: kubewarden
...
results:
- message: one of the containers has privilege escalation enabled
policy: cap-no-privilege-escalation
...
resourceSelector: {}
resources:
- apiVersion: apps/v1
kind: Deployment
name: nginx-deployment
namespace: default
...
result: fail
rule: no-privilege-escalation
source: kubewarden
timestamp:
nanos: 0
seconds: 1689017383
- policy: cap-do-not-run-as-root
...
resourceSelector: {}
resources:
- apiVersion: apps/v1
kind: Deployment
name: nginx-deployment
namespace: default
...
result: pass
rule: do-not-run-as-root
source: kubewarden
timestamp:
nanos: 0
seconds: 1689017383
...
summary:
error: 0
fail: 8
pass: 10
skip: 0
warn: 0