Audit Scanner - Policy Reports
When using the Kubewarden Audit Scanner, you store the results of policy scans using the OpenReports Custom Resources.
Since Kubewarden 1.30, PolicyReport Custom Resources ship as default but are marked as deprecated.
This page explains the usage of the new Reports and ClusterReports from OpenReports, which are functionally equal.
These CRDs offer a structured way to store and manage the audit results.
You store audit scanner policy scan results using Report and
ClusterReport. The audit scanner creates a Report or a
ClusterReport for each resource scanned, depending on the scope of the
resource. Report objects are available in the resource's namespace,
while ClusterReport objects are available in the cluster scope.
The audit results generated by the scanner include:
- the policy evaluated
- the resource scanned
- the result of the evaluation (pass, fail, or skip)
- a timestamp indicating when the evaluation took place.
You can also define severity and category annotations for your policies.
Operators can query the reports by using kubectl. They can also use the
optional UI provided by the
policy-reporter open-source
project for monitoring and observability of the OpenReports CRDs.
Querying the reports
Using the kubectl CLI, it's possible to query the results of the scan:
List the reports in the default namespace:
$ kubectl get report -o wide
NAME KIND NAME PASS FAIL WARN ERROR SKIP AGE
44da974b-6057-4745-a92c-9dd8a1b01cc4 Pod nginx-secrets 6 1 0 0 0 33m
...
List the cluster-wide reports:
$ kubectl get clusterreport -o wide
NAME KIND NAME PASS FAIL WARN ERROR SKIP AGE
6c66175f-e15f-47e8-8c33-2c63d5ecde3e Namespace namespace1 3 1 0 0 0 1h
d0ffbf4f-7348-4350-af7b-fdbfc079cc49 Namespace namespace2 0 4 0 0 0 1h
e48d9bbc-a9c4-4c36-8519-bc7390d9ec64 Namespace namespace3 4 0 0 0 0 15h
Get the details of a specific Report:
kubectl get report 44da974b-6057-4745-a92c-9dd8a1b01cc4 -o yaml
Get the details of a specific ClusterReport:
kubectl get clusterreport e48d9bbc-a9c4-4c36-8519-bc7390d9ec64 -o yaml
Report example
The following example shows a Report for the Deployment resource
deployment1 in the default namespace. The report indicates that the Pod
failed the safe-labels AdmissionPolicy.
apiVersion: openreports.io/v1alpha1
kind: Report
metadata:
creationTimestamp: "2025-10-20T12:28:01Z"
generation: 6
labels:
app.kubernetes.io/managed-by: kubewarden
kubewarden.io/audit-scanner-run-uid: 952e572e-0d37-4df2-a5ef-f41ced8e35eb
kubewarden.io/policyreport-version: v2
name: 82702633-0a9f-42b5-a9f4-b8eb58e46f03
namespace: default
ownerReferences:
- apiVersion: apps/v1
kind: Deployment
name: nginx-deployment
uid: 82702633-0a9f-42b5-a9f4-b8eb58e46f03
resourceVersion: "7883"
uid: 4ac9c589-d2a0-45f7-94e2-a6fd4642f06e
results:
- category: Resource validation
message: "The following mandatory labels are missing: cost-center"
policy: namespaced-default-safe-labels
properties:
policy-resource-version: "7385"
policy-uid: 6fda16f1-1843-41b5-994f-5141d92e7dd1
policy-name: "safe-labels"
policy-namespace: "default"
validating: "true"
resourceSelector: {}
result: fail
scored: true
severity: low
source: kubewarden
timestamp:
nanos: 0
seconds: 1760963881
scope:
apiVersion: apps/v1
kind: Deployment
name: nginx-deployment
namespace: default
resourceVersion: "7330"
uid: 82702633-0a9f-42b5-a9f4-b8eb58e46f03
source: ""
summary:
error: 0
fail: 1
pass: 0
skip: 0
warn: 0
ClusterReport example
The following example shows a ClusterReport for the Namespace
resource default. The report indicates that the resource has failed the
safe-annotations ClusterAdmissionPolicy validation.
apiVersion: openreports.io/v1alpha1
kind: ClusterReport
metadata:
creationTimestamp: "2025-10-20T12:34:00Z"
generation: 5
labels:
app.kubernetes.io/managed-by: kubewarden
kubewarden.io/audit-scanner-run-uid: 33496fad-9c53-404a-81aa-13d96c7235aa
kubewarden.io/policyreport-version: v2
name: e48d9bbc-a9c4-4c36-8519-bc7390d9ec64
ownerReferences:
- apiVersion: v1
kind: Namespace
name: kubewarden
uid: e48d9bbc-a9c4-4c36-8519-bc7390d9ec64
resourceVersion: "8258"
uid: 193af3fa-022f-49d2-ae8b-2e4fef1230f2
results:
- category: Resource validation
message: "The following mandatory annotations are not allowed: owner"
policy: clusterwide-safe-annotations
properties:
policy-resource-version: "7383"
policy-uid: 4d120a10-a303-4004-bb20-936c53f65cf3
policy-name: "safe-annotations"
validating: "true"
resourceSelector: {}
result: fail
scored: true
severity: low
source: kubewarden
timestamp:
nanos: 0
seconds: 1760964120
scope:
apiVersion: v1
kind: Namespace
name: kubewarden
resourceVersion: "423"
uid: e48d9bbc-a9c4-4c36-8519-bc7390d9ec64
source: ""
summary:
error: 0
fail: 1
pass: 0
skip: 0
warn: 0
Policy Reporter UI
The Policy Reporter is shipped as a subchart of kubewarden-controller.
Refer to the Audit Scanner Installation
page for more information.
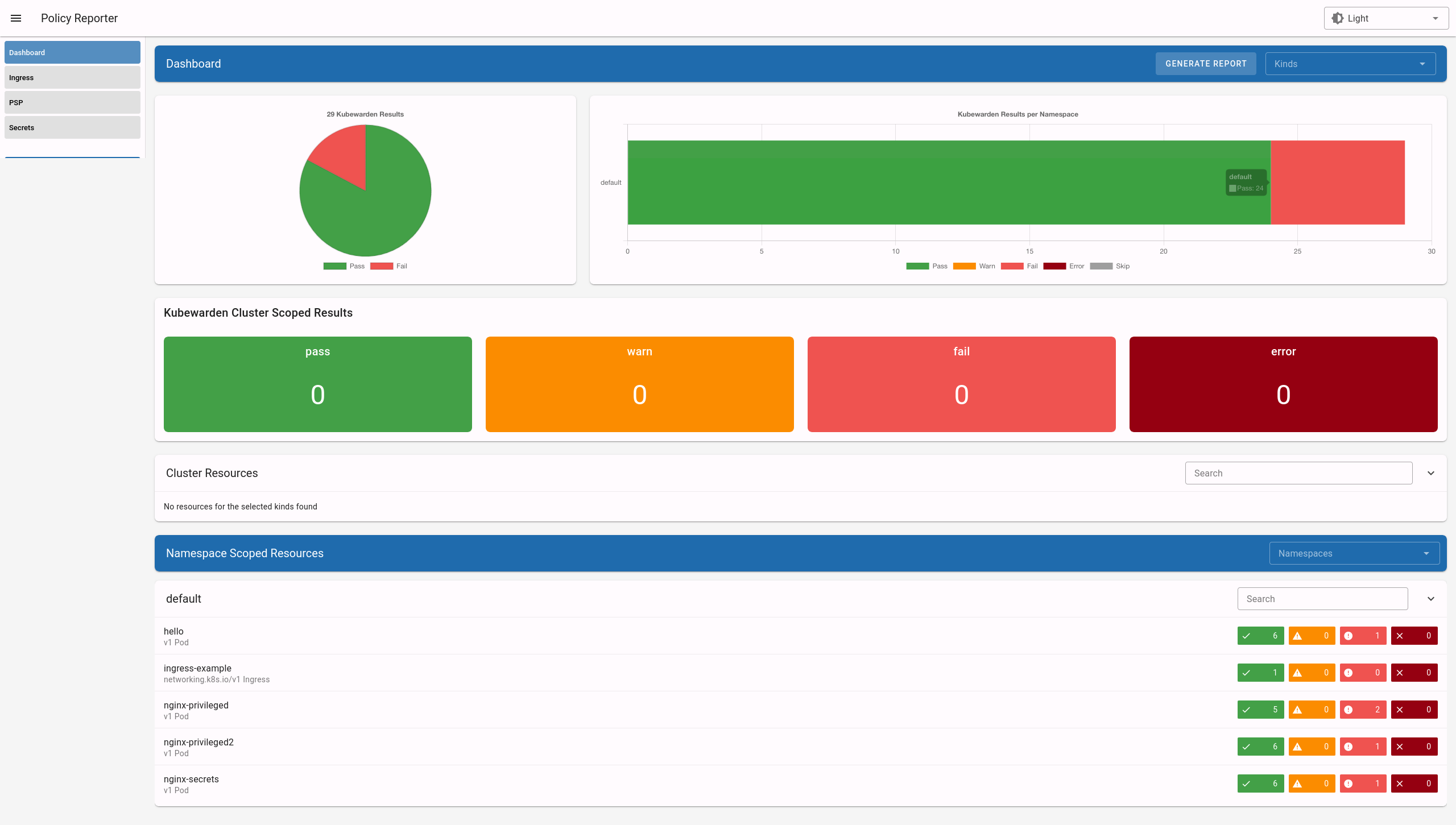
The Policy Reporter UI provides a dashboard showing all violations. See the screenshot below:
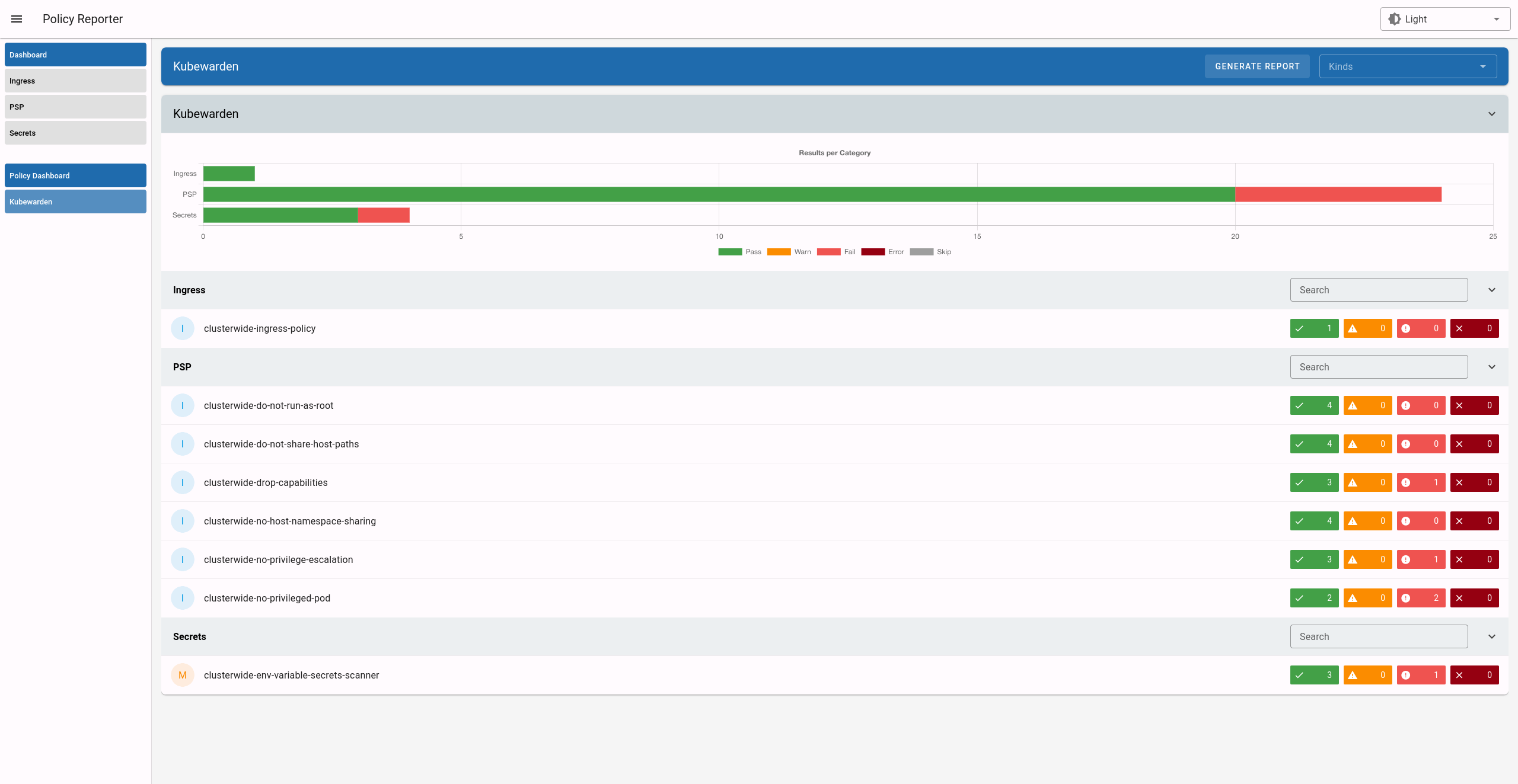
Kubewarden ships the Policy Reporter UI with a preconfigured filter that only shows Kubewarden policies, along with expanded information:
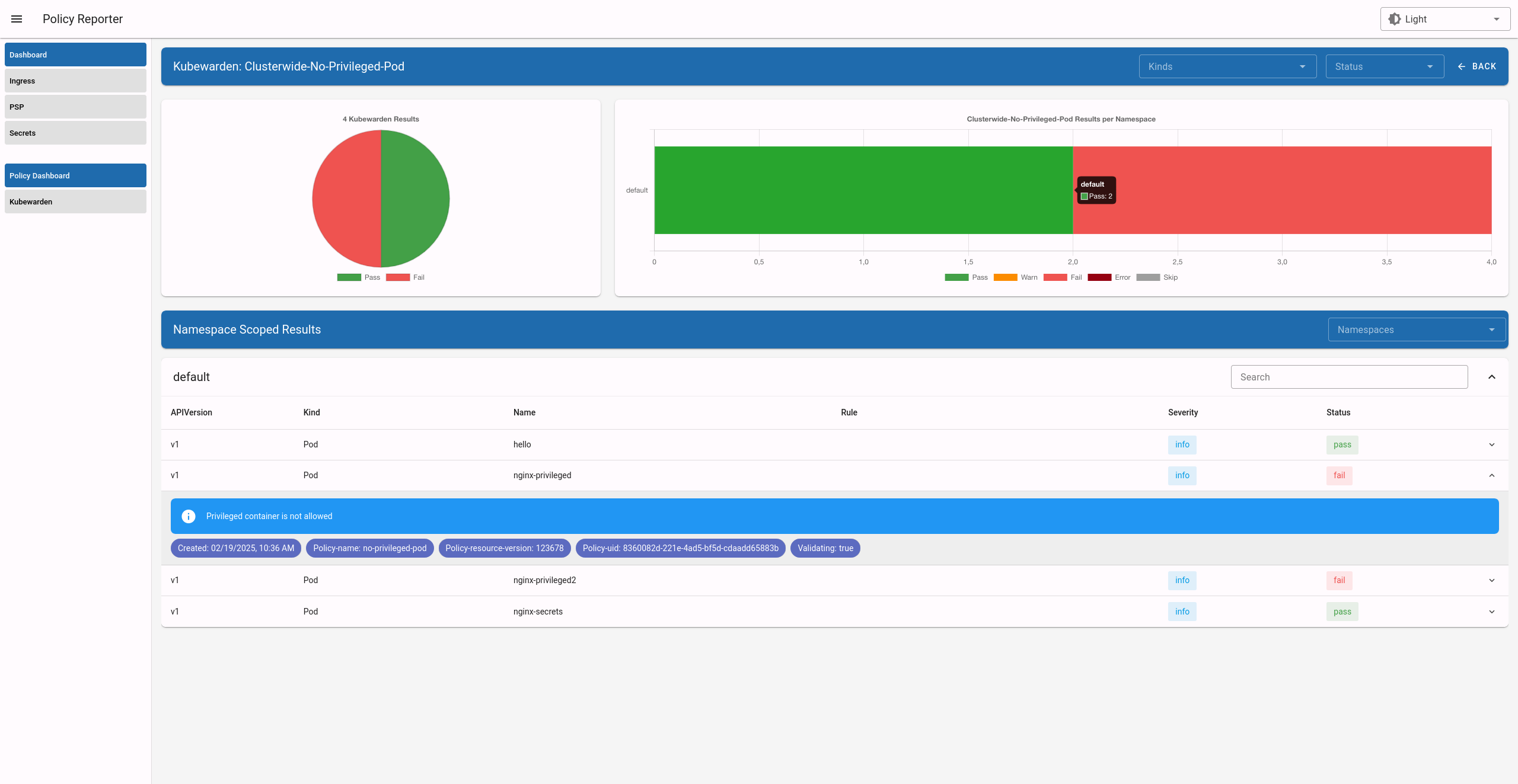
Click on a specific policy or resource to see a summary of results for it:
Other features of Policy Reporter include forwarding of results to different clients (like Grafana Loki, Elasticsearch, chat applications), metrics endpoints, and more. See the policy-reporter's community docs for more information.